The history of Bitcoin

On Oct. 31, 2008, an anonymous individual who went by the name of Satoshi Nakamoto published a white paper detailing a design for a “peer-to-peer electronic cash system,” a global financial infrastructure based on cryptographic proof instead of trust. Over a decade later, cryptocurrencies are now being discussed regularly in the context of global economic policy, with some nations even researching and developing their own digital currencies.
The underlying data structure of Bitcoin (BTC), often referred to as the blockchain, has also been researched and implemented in use cases ranging from supply chain management to logistics, cross-enterprise resource planning, energy trading, decentralized autonomous organizations and much more.
The purpose of this guide is to provide the newcomer with a comprehensive understanding of Bitcoin, covering the social and technological context of its inception, key events in its history, how it works, descriptions of its unique properties, and guides on how to participate within this new financial paradigm.
It is hoped that by the end of this guide, the reader will have a balanced perspective of one of the most fascinating technological and financial developments of the modern era.
The pre-history of Bitcoin
While the story often begins with the anonymous Satoshi publishing a white paper on Halloween 2008, there is an often neglected yet vibrant pre-history of Bitcoin that is essential to understanding it as a techno-social phenomenon decades in the making.
This guide to Bitcoin will begin by first charting the social and technical currents that led to its inception. Examining these currents is useful for discussing the past, present and future of Bitcoin.
The ideology of Bitcoin
While it might seem odd to suggest a Bitcoin ideology — considering its decentralized nature — the fact is that Bitcoin’s initial support base consisted mostly of tech-savvy individuals, libertarians and crypto-anarchists. Bitcoin’s inception and adoption within this community have come to define its values, virtues and fundamental design.
When Satoshi revealed their proposal for Bitcoin, it garnered just a small amount of interest and criticism from a very niche online community of cryptographers and computer scientists. Many of these individuals had been involved in digital cash experiments throughout the eighties and nineties.
To them, Bitcoin was simply the latest in a long sequence of experiments in creating monetary systems that respected individual freedom and privacy. In tracing the ideological roots back far enough, it can be found that Bitcoin’s formative influence largely stems from the discourse surrounding two particular communities.
Extropians
In 1988, a futurist named Max More put forth the philosophy of “extropianism” in a series of written principles that detailed an “evolving framework of values and standards for continuously improving the human condition” through the use of emerging technologies such as cryogenics, artificial intelligence, robotics, memetics, genetic engineering, space travel and more.
An extropian individual is someone who actively builds and tests these systems for the betterment of humanity while adhering to a strictly rationalist mindset unhindered by dogmatism. One of the core concepts of this community is life extension through the use of cryogenics, mind-uploading and other means.
This transhumanist ideology brought together a community of scientists and futurists who shared these ideas on early online forums. From the late eighties into the early to mid-nineties, the extropians prototyped designs for alternative currencies, idea markets, prediction markets, reputation systems and other experiments that foreshadowed much of the current crypto space. A number of cryptocurrency pioneers were active in the extropian community, including Nick Szabo and Hal Finney.
Cypherpunks
Similar to the extropians, the cypherpunks were united by a shared emphasis on technology to create a better world. The cyberpunk subgenre of sci-fi literature often portrays a future in which a global cabal of corporations effectively rules the world through ubiquitous surveillance systems, with the protagonists often being hackers or other individuals maneuvering through this dystopian society.
The cypherpunks were so called because they saw the works of authors John Brunner, William Gibson and Bruce Sterling as plausible scenarios given the trends in sociopolitical progress and technological innovation. They believed that the rise of global computer networks mediated by governments and corporations would systematically compromise liberty and freedom.
The cypherpunks were a community of cryptographers, computer scientists and futurists dedicated to building the systems necessary to secure individual sovereignty amid a potential surveillance state.
Contrary to the extropians, the cypherpunks emphasized a particular set of technologies around encrypted communication networks, including anonymous messaging and electronic money. Many of the digital currency experiments throughout the 1990s and early 2000s were directly driven by the cypherpunk movement. This community is the soil from which Bitcoin grew.
Bitcoin’s technical lineage
The key to understanding Bitcoin is realizing it not as a singular, unique invention but a clever synthesis of prior work that succeeded where past efforts failed. Satoshi sought to build a trust-minimized financial infrastructure that could persist years into the future.
Instead of building a new solution in a vacuum, he built upon past research in distributed systems, financial cryptography, network security and more. First, this guide will describe the foundational technology of “crypto.” Then, it will describe some of the digital cash experiments that preceded and influenced Bitcoin.
Public key cryptography
For centuries, cryptography, or the technology of secret-sharing, relied on multiple parties to agree on a shared private key to decrypt messages. This is known as symmetric key encryption. This method consistently ran into the problem of key distribution. Past methods included face-to-face meetings or the use of a trusted courier. Not only was this system vulnerable on many points, but it was also impractical to implement at scale.
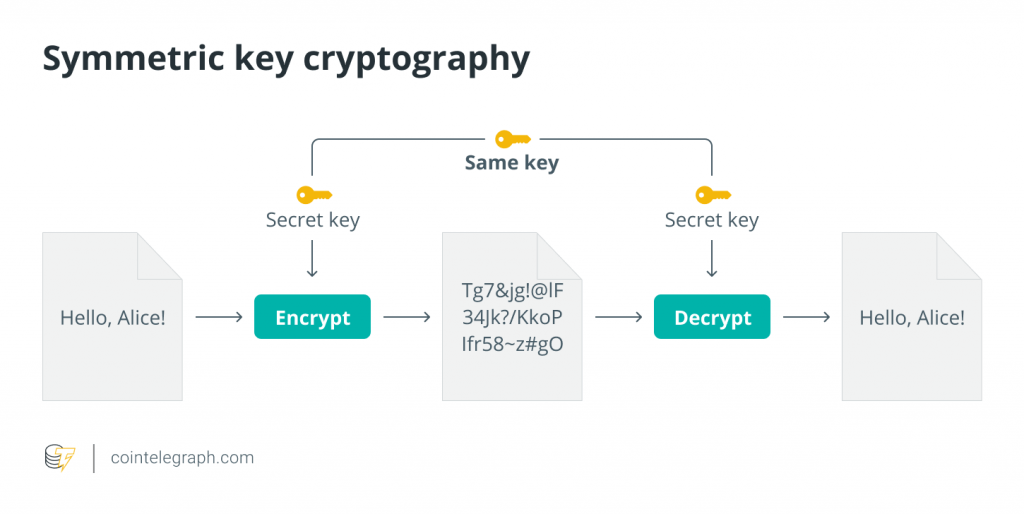
In the 1970s, an alternative method of secret-sharing emerged known as asymmetric key encryption, or public key cryptography. In this system, each party would have a pair of public and private keys. If Alice wanted to send a secure message to Bob, she would encrypt the message with Bob’s known public key. Bob would then decrypt Alice’s message with his own private key. In this system, neither party has to agree on a shared secret in advance. Alice can also digitally sign her message to Bob using her private key, allowing Bob or anyone else with knowledge of her public key to verify the message’s authenticity.
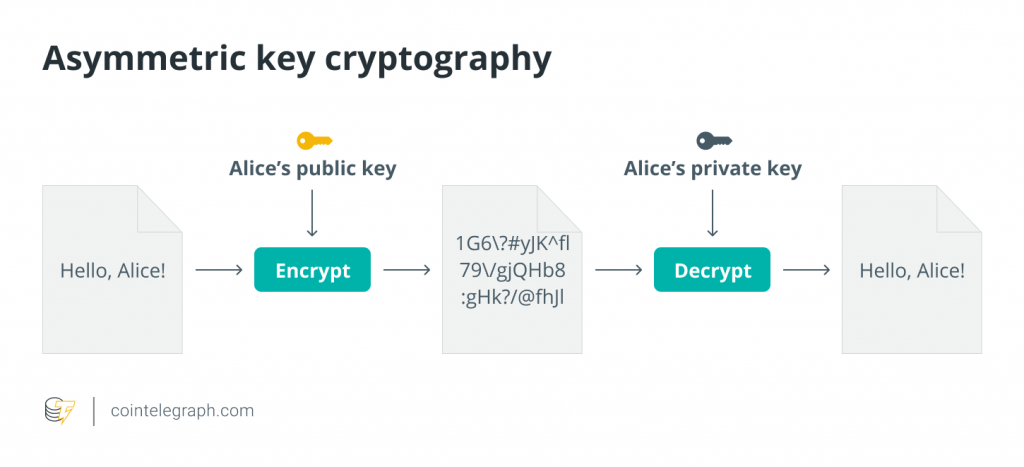
This combination of public key cryptosystems and digital signatures is the bedrock technology of what is now broadly called “crypto” and has successfully secured communication networks and the protocols that comprise the internet for decades. It is also a key element in digital cash systems.
The Crypto Wars
It is important to note that public key cryptography was discovered nearly simultaneously in the 1970s by the United Kingdom’s Government Communications Headquarters and by two independent American researchers named Whitfield Diffie and Martin Hellman. Governments had no intention of giving the public access to privacy-preserving technologies like public key cryptography, as it would fundamentally shift the balance in power.
When the World Wide Web arrived in the nineties, creating an explosive demand for online messaging and e-commerce, governments pushed back against the adoption of encryption by the masses, citing concerns around security and criminal activity.
Known unofficially as the Crypto Wars, this era of friction between governmental powers and the entrepreneurs and builders of a new technological paradigm echoes to the present day as governments are forced to acknowledge the emergence of a borderless, leaderless financial system heralded by Bitcoin.
eCash
David Chaum is perhaps the most influential person in the cryptocurrency space. His pioneering work in digital currency systems dates back to the eighties when the internet was still in its nascent stages before the launch of the World Wide Web.
In 1981, Chaum published a groundbreaking paper, “Untraceable Electronic Mail, Return Addresses, and Digital Pseudonyms” — a foundational document in the realm of privacy on the internet that directly led to the creation of privacy protocols such as Tor. In 1982, Chaum published “Blind Signatures for Untraceable Payments,” a keystone document that detailed an anonymous transaction system that would directly inspire future digital currency experiments.
The eCash payments system was Chaum’s attempt at bringing the privacy of physical cash and coins to the digital realm with the advent of electronic banking services. In 1989, Chaum founded DigiCash. Headquartered in Amsterdam, Chaum and his team built out the eCash protocol. Throughout the latter half of the nineties, Chaum struggled to secure enough partnerships with merchants and banks to sustain the project and ended up declaring bankruptcy in 1998.
While the venture didn’t last, eCash blazed new trails in the digital currency space. While not a natively digital currency like Bitcoin, eCash foreshadowed what have now come to be known as central bank digital currencies, or CBDCs, and stablecoins — digital assets backed by reserves and issued by a trusted third party such as a bank or corporation.
E-gold
Founded by Douglas Jackson and Barry Downey in 1996, E-gold was a digital currency system backed by gold reserves in vaults in London and Dubai. Denominated in grams, E-gold provided an alternative online payments system capable of fast, borderless value transfer, but the project faced significant legal and systemic issues.
The E-gold economy was conducted via a central server maintained by a single company, which produced a single point of failure or disruption in the event of a dispute between operators or shutdown/seizure by authorities. The E-gold system originally didn’t have many restrictions in terms of account creation, which lead to the currency being used in various criminal activities. While Jackson and the team made efforts to counter the criminal use of E-gold, they were ultimately found guilty of running an unlicensed money transmission enterprise, and the venture was shut down.
Whereas eCash was an electronic currency system implemented in coordination with the legacy banking system, E-gold was operating as a parallel financial system built entirely without the acknowledgment or input of regulatory authorities. During this time, the United States government was wary of the public having access to public key cryptography and the means to encrypt their presence on the internet. Ventures like E-gold brought such concerns to the act of transacting over communication networks. Much of the regulatory friction around alternative digital currencies that sparked during this time has persisted to this day.
Peer-to-peer digital cash: Cypherpunk edition
While the previous digital currency systems were influential in the design of electronic cash, the builders were not directly involved with that community. Chaum, for example, did not particularly subscribe to the cypherpunk ideology.
The following digital cash experiments, however, were conceived by active members of this community and can be seen as direct precursors to Bitcoin. Either directly or indirectly, these proposals and implementations were influential to Satoshi’s invention of Bitcoin.
Hashcash
In 1992, IBM researchers Cynthia Dwork and Moni Naor were exploring methods for combatting Sybil attacks, denial-of-service attacks and spam messaging on burgeoning internet services such as email. In their paper “Pricing via Processing or Combatting Junk Mail,” the pair proposed a system in which a sender of an email conducts some amount of computational work to solve a cryptographic puzzle.
The sender would then attach proof of the solution to the email: a proof-of-work, or PoW. While the computational cost of this process was fairly trivial, it would be enough to effectively inhibit spam. The system would also feature a “trapdoor” that would allow a central authority to instantly solve the puzzle without expending work.
In 1997, 26-year-old University of Exeter graduate and active cypherpunk Adam Back took to the cypherpunk mailing list and proposed a similar system called Hashcash. In this system, there was no trapdoor, central authority or emphasis on cryptographic puzzles. Instead, the process centered around hashing.
Hashing is the process of turning any piece of data of any size into a random string of characters of predetermined length. The slightest change to the underlying data would result in an entirely different hash, allowing for easy data verification. For example, a SHA-256 hash of the phrase “What is Bitcoin?” produces the following hexadecimal number:
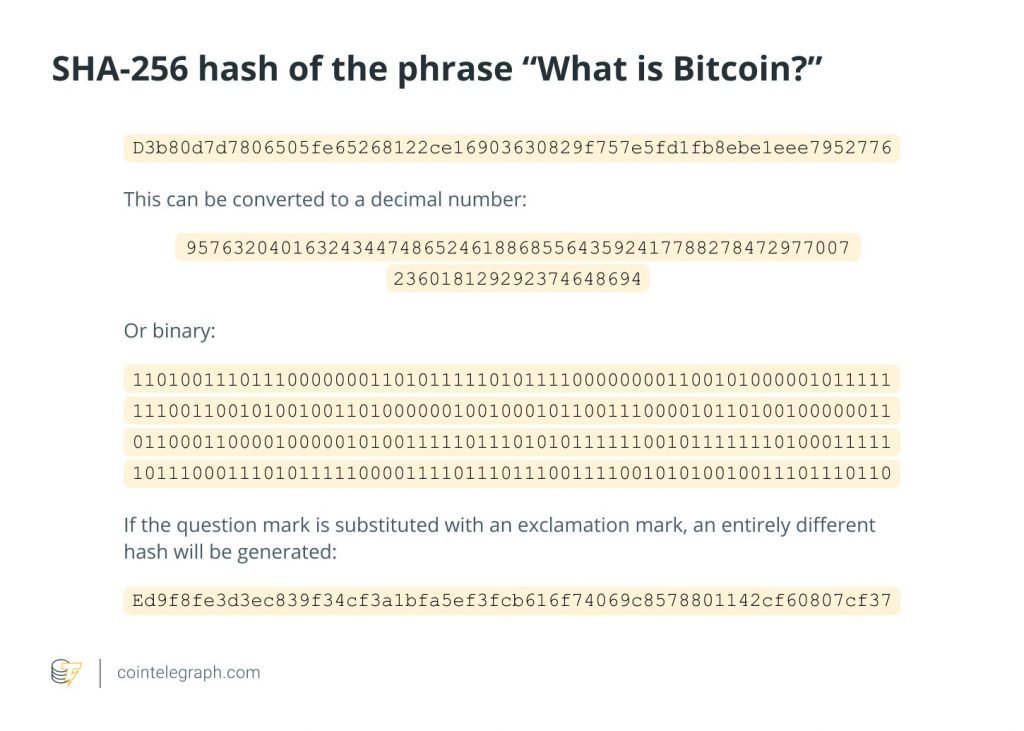
In Hashcash, a sender would repeatedly hash the metadata of the email — such as the sender’s address, the receiver’s address, the time of the message, etc. — along with a random number called a “nonce” until the resultant hash begins with a predetermined number of zero bits.
Because the sender can’t know the correct hash off the bat, they must then repeatedly hash the email metadata using a different nonce until a valid combination is found. Similar to Dwork and Naor’s system, this process requires computational resources, generating a proof-of-work.
As the name indicates, anti-spam was not the only use case Back had in mind for Hashcash. However, the proof-of-work tokens were useless to the recipient and could not be transferred, rendering them ineffective as digital cash. The currency would have also been subject to hyperinflation, as the ever-improving computation speed of new machines would make generating proofs easier and easier. Nevertheless, Back’s Hashcash would inspire the further application of proof-of-work in two proposed digital cash systems and precursors to Bitcoin: B-money and Bit Gold.
B-money
In 1998, active cypherpunk Wei Dai proposed B-money, an alternative peer-to-peer, or P2P, financial system for conducting online commerce outside of the legacy financial system controlled by enterprise gatekeepers and regulated by governments. The system would allow for the creation of digital currency and the enactment and enforcement of contracts complete with an arbitration system to resolve disputes. Dai’s post consisted of two proposals.
Dai’s first proposal removed the central authority’s singular control of a transactional database and replaced it with a shared ledger system among a network of pseudonymous peers represented as public key addresses. To mint a digital currency, a node would have to solve a computational problem and broadcast the solution to the network (a proof-of-work) in a multiphase auction. The number of assets issued would be determined by the cost of computation effort undertaken in relation to a basket of standard commodities.
If Alice wanted to transact with Bob, she would broadcast a transaction to the entire network that includes a packet of information containing the amount and Bob’s public key address. However, Dai realized that this initial proposal did not solve the double-spend problem because it would be possible for Alice to simultaneously spend the same assets with Bob and Carol.
In his second proposal, Dai suggested that instead of everyone having a copy of the ledger, a special subset of peers, called “servers,” would maintain a shared ledger while regular users simply verified that the transactions had been processed by the server. To ensure trust and prevent collusion, servers would deposit a certain amount of money in a special account, which would be used as a fine or reward in the event of malicious behavior, similar to proof-of-stake systems in other blockchains.
Dai’s proposal for B-money was never implemented in any way, yet what is striking about it is how similar to Bitcoin it was, particularly with the use of the shared ledger and PoW-based digital currency. The main difference, however, was that B-money’s currency was tied to a certain value of commodities, making it an early model for what would now be called a stablecoin.
Bit Gold
Formerly an active member of both the extropian and cypherpunk communities, Szabo is one of the most influential figures in the development of cryptocurrency and blockchain technology. He is a polymath traversing disciplines ranging from computer science and cryptography to law.
Szabo’s North Star is the vision of creating a free economic society outside the control of corporations and nation-states. In 1994, he proposed smart contracts — essentially, digital contracts executed and enforced via code rather than jurisdictional law — as a fundamental building block of borderless e-commerce.
He later realized that a key element was missing: a natively digital currency that could flow through these contracts. After witnessing a litany of digital cash experiments face obstacle after obstacle (and even working at Chaum’s DigiCash for a time), Szabo decided to work on a new proposal that could succeed where past efforts failed.
In studying the history of money, Szabo identified commodity money like gold bullion bits as a strong conceptual foundation for a new currency of the internet. This new money had to be digital, scarce, incredibly costly to forge and not rely on trusted third parties to secure it and give it value — a digital gold, in a sense. His proposal: Bit Gold.
Bit Gold works similarly to Hashcash and particularly B-money in that it uses an accumulating chain of hash-based proofs-of-work that is periodically timestamped and published to a network of servers. The issuance and ownership of Bit Gold are recorded on a distributed property title registry — basically, a protocol that allows for the governance of certain classes of property using a quorum-based voting system.
Where Bit Gold fell short as a currency was its lack of fungibility — i.e., when each individual unit is interchangeable for an identical unit for the same value. This is essential for any viable form of currency. Because the cost of a Bit Gold is related to the computational cost of the proof-of-work at a specific moment in time, and because the cost of computation would decrease with better machines, a unit of Bit Gold mined in 2015 would be worth less than a unit of Bit Gold mined in 2005.
Szabo proposed a second-layer solution involving a secure, trusted, auditable bank that could track the issuance of Bit Gold over time, continuously packaging the proof-of-work tokens into equal units of value, creating a stable medium of exchange. However, the system would be susceptible to Sybil attacks that could cause a split in the network. Szabo believed any potential network split could be fixed with the honest participants continuing on their own system and that the users would naturally side with them through social consensus.
Szabo was gearing up to finally implement Bit Gold shortly before Satoshi published the design for Bitcoin in 2008. After Bitcoin launched, he abandoned the Bit Gold project, believing that Bitcoin cleverly solved the shortcomings of Bit Gold and prior digital cash experiments by synthesizing prior attempts into a system that simply worked.
These two digital cash experiments were crucial to the invention of Bitcoin. In a 2010 Bitcointalk forum post, Satoshi stated, “Bitcoin is an implementation of Wei Dai’s B-money proposal […] in 1998 and Nick Szabo’s Bitgold proposal.”
The birth of Bitcoin
While entire books and podcasts have covered the history of Bitcoin in great detail, for the purposes of this guide, only the landmark moments in Bitcoin’s history will be covered, and their significance within the evolving story of cryptocurrency will be unpacked.
Security
“When we can secure the most important functionality of a financial network by computer science rather than by the traditional accountants, regulators, investigators, police, and lawyers, we go from a system that is manual, local, and of inconsistent security to one that is automated, global, and much more secure.”
— Nick Szabo, “Money, Blockchains, and Social Scalability”
Security is essential for large-scale information and communication systems. The internet was originally conceived to be a communications network capable of withstanding nuclear war. While the geopolitical context and core intentions are quite different, Bitcoin was also designed to operate in an adversarial, unstable environment.
The network’s security model was inspired by decades of research and development around securing the integrity and uptime of distributed systems. Truly peer-to-peer computer systems present unique challenges and risks in this area because there are no central administrators that can be trusted to right the ship. Robust security is incredibly important for the Bitcoin network because it facilitates an entire monetary system with immense value at stake.
Bitcoin’s proof-of-work consensus system safeguards the network from Sybil attacks (the creation of numerous fake accounts to swarm and overwhelm the network) and intermittent or faulty nodes (from power outages or poor maintenance), resulting in a Byzantine fault-tolerant system.
Byzantine fault tolerance is the capacity of a distributed system to maintain consensus with imperfect information, partial network failure or even malicious agents. The term is a reference to the scenario articulated by Leslie Lamport, Robert Shostak and Marshall Pease in their influential paper “The Byzantine Generals Problem,” in which they use the example of a group of army generals coordinating in a battlefield environment with limited means of communication.
With imperfect information and situational awareness, how can the generals agree and execute on a shared strategy or even trust that another general will not turn traitor and single-handedly turn the tide of battle? Their conclusion: As long as at least two-thirds of the generals are loyal, the effort will not be self-defeating.
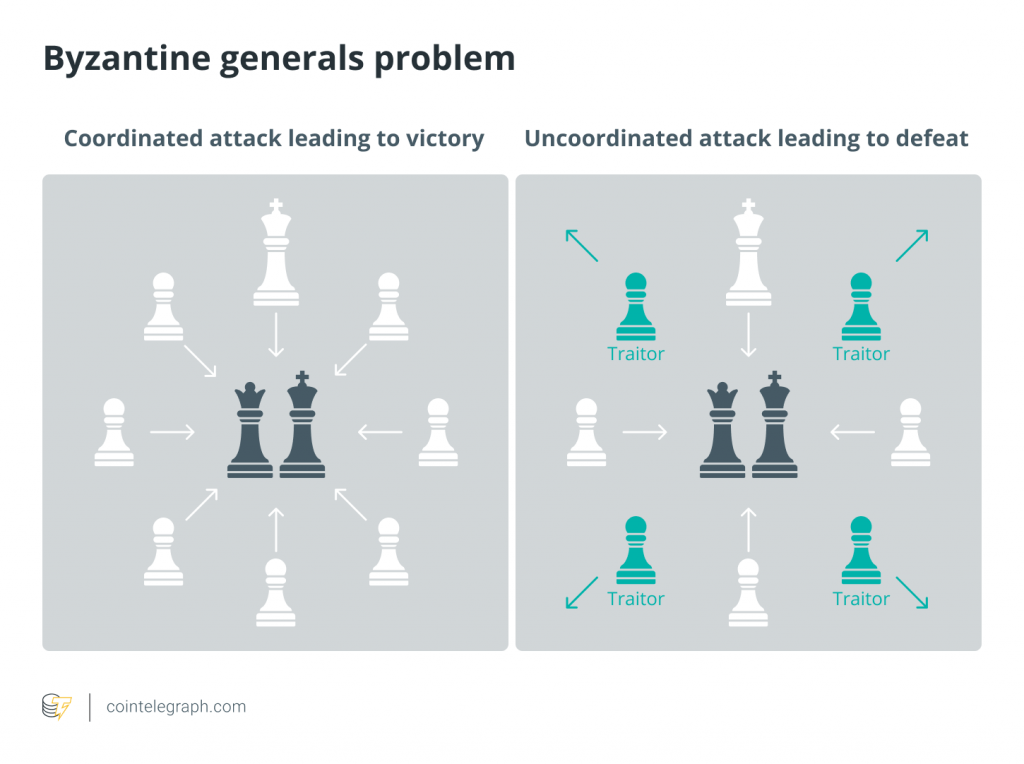
As discussed previously, Bitcoin’s decentralization is made possible by a clever alignment of incentives between the network’s stakeholders: miners, developers, merchants and users. Simply put, any concerted attempt to capture the network or reorganize the chain would result in the value of the currency plummeting, thus rendering any intended benefit completely worthless.
The cost of being a bad actor significantly outweighs any possible reward. Thus, it is in every participant’s best interest to simply play by the rules and collectively work toward the maturation and adoption of the Bitcoin ecosystem.
Since its launch in January 2009, the Bitcoin network has never been compromised at the base layer and has had effectively 0% downtime, making it one of the most secure computer systems on the planet.
Anonymity/pseudonymity
One of Bitcoin’s core characteristics is that it forgoes the account-based model of identifying participants in the network and substitutes it for a public key cryptosystem where entities are represented by cryptographic key pairs rather than assigned names. Bitcoin addresses are strings of 26 to 35 alphanumeric characters that begin in either 1, 3 or bc1. While there are services that allow users to map names to their public key addresses to make them more user-friendly, the default user experience of Bitcoin involves interacting with these cryptographic key pairs.
Cryptographic keys are essential to privacy online and have been a fundamental building block of privacy-preserving systems ranging from digital cash, to email, to routing protocols such as Tor. They are omnipresent throughout the numerous information and communication technologies that permeate our lives, but many systems abstract the experience with the keys managed and coordinated by trusted third parties rather than directly by users.
This emphasis on cryptographic keys as a primitive for private communications and transactions online was heavily influenced by the cypherpunks. Timothy May’s manifesto, in particular, highlights the revolutionary capacity of giving individuals the ability to anonymously transact with and message each other on communications networks with digital signatures being the sole method of verification — no identities needed.
In the context of Bitcoin, cryptographic key pairs are not simply a substitute for identity but also an asset in and of themselves. Commonly referred to as wallets, as they allow one to send and receive Bitcoin between other public key addresses, these keys are digital bearer assets that grant the holder sole ownership of the underlying assets. As the motto goes: “Not your keys, not your crypto.” One of Bitcoin’s most revolutionary qualities is the realization of true ownership and management of one’s assets without relying on custodial services provided by trusted third parties.
But how does Bitcoin’s privacy model fares against modern-day solutions? While Bitcoin’s privacy has been one of the currency’s defining traits over the years and a frequent point of friction with regulators, data analytics of blockchains has advanced enough that casual use of Bitcoin has effectively become de-anonymized.
Because all transaction data is publicly available, applying sophisticated analytics techniques to a transaction graph can link public key addresses to various external accounts, including exchanges and other fiat on/off-ramps. Solutions for securing anonymity, such as cryptocurrency mixers, can help obfuscate the transaction flow and prevent linkage to external accounts and real-world identities, but these tools have begun to face active government shutdown. Much of the Bitcoin protocol’s forward development is focused on reinforcing its privacy features.
Transparency
The Bitcoin newcomer may be thrown off guard by Bitcoin’s qualities as both a (mostly) privacy-preserving system and a transparent one. Aren’t these two characteristics mutually exclusive? Not necessarily. In fact, it is the equilibrium of these two qualities that makes Bitcoin and blockchain particularly effective and useful as an open financial system.
We’ve established that Bitcoin’s privacy model is founded by substituting names and accounts with cryptographic key pairs. These key pairs are the tools by which users transact with one another securely on the network via digital signatures. If we don’t know the identity of those we’re transacting with, then how do we trust that the record is true?
With blockchain, these transaction flows and the chains of ownership of these valuable bits are preserved in a shared ledger of cryptographically verifiable, secure data. The combination of a mutual ledger of secure yet open data and a consensus system that allows the peers on the network to continuously agree on the valid state of this ledger results in one of blockchain’s core value propositions: data verification.
If all the peers on the network share a transaction record going back to the genesis block and the cost of reverting previously timestamped transactions outweighs any benefits by an exponential degree, then participants in the Bitcoin network can trust the validity of the ledger rather than each other or a trusted third party.
While there is much emphasis on financial transactions on the Bitcoin network for obvious reasons, the blockchain has proven quite useful for other applications as well. The first nonfinancial application of the Bitcoin blockchain was proof-of-existence, a method of using the Bitcoin blockchain to timestamp documents and other digital files by associating the hash of a piece of data with an owner’s private key, denoting ownership, agreement or consent around a certain action or bit of information.
The use cases range from the documentation and enforcement of legal contracts, to the provenance of data surrounding a digital or physical asset, to the implementation of a global, automated notary public.
Speed
When we talk about Bitcoin’s speed, there is an important distinction to make. Are we talking about the number of transactions Bitcoin can process over a certain amount of time or the amount of time required to process a single transaction? These are related but distinct observations in assessing the value proposition of Bitcoin in relation to time.
A common measurement for quantifying a cryptocurrency’s speed and scalability is transactions per second. At the time of writing this guide, the Bitcoin network averages merely 4 tx/s, an incredibly small sum that pales in comparison to Visa’s roughly 1,700 tx/s. The discourse around Bitcoin’s scalability and viability as digital cash tends to refer to this number.
On the other hand, how long does it take for Alice to send Bitcoin to Bob? While this depends on the amount in transaction fees paid by Alice to incentivize priority validation by miners, the average block time is roughly 10 minutes, with transaction finality certain after 6 blocks, or 60 minutes.
While there is much room for improvement in Bitcoin’s transaction throughput and confirmation times, it is important to keep in mind that these are peer-to-peer transactions executed and secured by a global network operating beyond borders. This is key to understanding Bitcoin’s value proposition. While it is currently lacking in raw speed, Bitcoin foregoes the central clearinghouses necessary for processing Visa and ACH bank transfers in favor of an ultra-secure global settlement layer. Within an hour, millions of dollars in value can be sent across the world and verified with minimal fees and without the use of trusted third parties.
In the short to medium term, maturing layer-two scaling solutions like Lightning will provide a trust-minimized means for conducting high-frequency Bitcoin transactions off-chain with the security of the Bitcoin blockchain.
